hi viks
Its all about Computer science. Latest Techno Information. New Techno Release Info, Techno tips, Programming Articles and codes, Old and New tricks, Product reviews etc.
Pages
Popular Posts
- Techno Sparks: TuneUp Utilities 2012 v12.0 Final Incl Keymaker-CORE
- A trick to create an undeleatable and secure folder
- interface exapmle in java
- 10 less-known but awesome Google products
- Cellphones, Software, GPS, Intel to acquire Telmap, dole out easy to implement location APIs to AppUp developers
- Tic Tack Toi game in c
Monday, July 14, 2014
Friday, November 23, 2012
Windows Lodar...
This software can activate windows 7 any version easly
https://www.dropbox.com/s/51t7a1p2rgyfya7/Windows%20Loader.rar
https://www.dropbox.com/s/51t7a1p2rgyfya7/Windows%20Loader.rar
Saturday, September 29, 2012
java script quick reference guide
| The most advance book for all java script programer a quick reference guide to java script, hope you all will enjoy.. |
Download link:
interface exapmle in java
* program to impliment interface
* @author vikas
* @version 1.00 2012/9/28
*/
interface shape{
public String bclass="shape";
public void draw();
}
* @author vikas
* @version 1.00 2012/9/28
*/
interface shape{
public String bclass="shape";
public void draw();
}
Wednesday, September 26, 2012
10 less-known but awesome Google products
10 less-known but awesome Google products

Cookin with Google
This customised search lets you find recipes from across the world. Through this page, Google will only search through food sites that provide recipes and remove useless links that just have the search terms mentioned. The results you get can be further filtered using various heads — special recipes for diabetics, low-fat recipes, for vegetarians for weight watchers and so on.
http://goo.gl/0oCea
 |
Navigation & Traffic
Monday, September 24, 2012
Tic Tack Toi game in c
#include<graphics.h>
#include<iostream.h>
#include <conio.h>
void main()
{
start: int a[3][3]={5,6,7,8,9,10,11,12,13},i,j,k,x,y,t,cn=0,co=0;
char c;
static int nod=0,nn=0,sc[2]={0,0};
nod++;
clrscr();
int driver=DETECT,mode;
#include<iostream.h>
#include <conio.h>
void main()
{
start: int a[3][3]={5,6,7,8,9,10,11,12,13},i,j,k,x,y,t,cn=0,co=0;
char c;
static int nod=0,nn=0,sc[2]={0,0};
nod++;
clrscr();
int driver=DETECT,mode;
Bresenham's line drawing code in c
# include <stdio.h>
# include <conio.h>
# include <graphics.h>
void main()
{
int dx,dy,x,y,p,x1,y1,x2,y2;
int gd,gm;
clrscr();
printf("\n\n\tEnter the co-ordinates of first point : ");
scanf("%d %d",&x1,&y1);
printf("\n\n\tEnter the co-ordinates of second point : ");
scanf("%d %d",&x2,&y2);
# include <conio.h>
# include <graphics.h>
void main()
{
int dx,dy,x,y,p,x1,y1,x2,y2;
int gd,gm;
clrscr();
printf("\n\n\tEnter the co-ordinates of first point : ");
scanf("%d %d",&x1,&y1);
printf("\n\n\tEnter the co-ordinates of second point : ");
scanf("%d %d",&x2,&y2);
Bresenham Circle drawing program in c
# include<stdio.h>
# include<conio.h>
# include<graphics.h>
# include<math.h>
void main()
{
int gd=DETECT,gm;
int r,x,y,p,xc=320,yc=240;
initgraph(&gd,&gm,"C:\\TC\\BGI");
cleardevice();
printf("Enter the radius ");
scanf("%d",&r);
x=0;
# include<conio.h>
# include<graphics.h>
# include<math.h>
void main()
{
int gd=DETECT,gm;
int r,x,y,p,xc=320,yc=240;
initgraph(&gd,&gm,"C:\\TC\\BGI");
cleardevice();
printf("Enter the radius ");
scanf("%d",&r);
x=0;
Friday, April 20, 2012
AVL tree, insertion in avl tree
 This is a program of insertion in avl tree and checking the weight of nodes then performing further operations hope it will help you.
This is a program of insertion in avl tree and checking the weight of nodes then performing further operations hope it will help you./*Program for insertion in AVL tree*/
#include<stdio.h>
#include<malloc.h>
typedef enum {
FALSE ,TRUE } bool;
struct node
{
int info;
int balance;
struct
node *lchild;
struct
node *rchild;
};
struct node
*insert (int , struct node *, int *);
struct node*
search(struct node *,int);
Monday, April 16, 2012
Phone bill project in c , phone bill in c
Phone Bill System Project
# include <conio.h>
# include <stdio.h>
# include <alloc.h>
# include <string.h>
struct node
{
int num;
char name[15];
struct node *next;
};
struct node *list; //global start pointer
FILE *fp; // Global file pointer
struct node *getrecord()
{
struct node *temp,e;
temp=(struct node*)malloc(sizeof(struct node));
printf("Reached till here...");
getch();
fflush(stdin);
// fscanf(fp,"%d %s
",&temp->num,temp->name);
fread(&temp,sizeof(temp),1,fp);
printf("%d %s",temp->num,temp->name);
// temp->num=e.num;
// strcpy(temp->name,e.name);
getch();
temp->next = NULL;
return temp;
}
struct node *getnode()
{
struct node *temp;
temp = (struct node*)malloc(sizeof(struct node));
printf("
Enter the person's phone number--->");
scanf("%d",&temp->num);
printf("
Enter the person's Name--->");
scanf("%s",&temp->name);
temp->next = NULL;
return temp;
}
struct node *search(int id,int *flag)
{
struct node *cur,*prev;
*flag=0;
if
(list==NULL)
return NULL;
for(prev=NULL,cur=list; (cur); prev=cur,cur=cur->next)
if(cur->num == id)
{
*flag = 1;
break;
}
# include <stdio.h>
# include <alloc.h>
# include <string.h>
struct node
{
int num;
char name[15];
struct node *next;
};
struct node *list; //global start pointer
FILE *fp; // Global file pointer
struct node *getrecord()
{
struct node *temp,e;
temp=(struct node*)malloc(sizeof(struct node));
printf("Reached till here...");
getch();
fflush(stdin);
// fscanf(fp,"%d %s
",&temp->num,temp->name);
fread(&temp,sizeof(temp),1,fp);
printf("%d %s",temp->num,temp->name);
// temp->num=e.num;
// strcpy(temp->name,e.name);
getch();
temp->next = NULL;
return temp;
}
struct node *getnode()
{
struct node *temp;
temp = (struct node*)malloc(sizeof(struct node));
printf("
Enter the person's phone number--->");
scanf("%d",&temp->num);
printf("
Enter the person's Name--->");
scanf("%s",&temp->name);
temp->next = NULL;
return temp;
}
struct node *search(int id,int *flag)
{
struct node *cur,*prev;
*flag=0;
if
(list==NULL)
return NULL;
for(prev=NULL,cur=list; (cur); prev=cur,cur=cur->next)
if(cur->num == id)
{
*flag = 1;
break;
}
Thursday, April 12, 2012
4G launch in INDIA
Know about 4G
 Bharti Airtel on Tuesday become the first company in India to offer high-speed Internet services using fourth-generation (4G) telecommunications technology.
Bharti Airtel on Tuesday become the first company in India to offer high-speed Internet services using fourth-generation (4G) telecommunications technology.The company said high-speed wireless broadband "has the potential to transform India" and to provide a platform for "building the country's digital economy."
What's new in 4G technology?
Visual Studio 2011 beta
 Microsoft launches Visual studio 2011 beta. It's an awesome release after visual studio 2010. Much advance than its previous versions, start with an awesome installation screen minimal user interaction required for installing it takes about 10GB of disk space. And take about more than 30 min. to install in my system dual core it take 45 min. . After installing when i launched it takes 35 sec to start in full mode.
Microsoft launches Visual studio 2011 beta. It's an awesome release after visual studio 2010. Much advance than its previous versions, start with an awesome installation screen minimal user interaction required for installing it takes about 10GB of disk space. And take about more than 30 min. to install in my system dual core it take 45 min. . After installing when i launched it takes 35 sec to start in full mode.Try it
http://www.microsoft.com/visualstudio/11/en-us/downloads#vs
Monday, April 9, 2012
How to use Problem Steps Recorder in Windows 7?
How to use Problem Steps Recorder in Windows 7?
The Problem Steps Recorder in the Windows 7 operating system is a feature that enables users to record their interactions with an application and provide a detailed screen-by-screen view with accompanying information. We can use Problem Steps Recorder to automatically capture the steps We take on a computer, including a text description of where we clicked and a picture of the screen during each click (called a screen shot). Once we capture these steps, We can save them to a file that can be used by technical team or someone else helping you with a computer problem.
Step 1. Open Problem Steps Recorder by clicking the Start button, and then typing psr.
The Problem Steps Recorder in the Windows 7 operating system is a feature that enables users to record their interactions with an application and provide a detailed screen-by-screen view with accompanying information. We can use Problem Steps Recorder to automatically capture the steps We take on a computer, including a text description of where we clicked and a picture of the screen during each click (called a screen shot). Once we capture these steps, We can save them to a file that can be used by technical team or someone else helping you with a computer problem.
Step 1. Open Problem Steps Recorder by clicking the Start button, and then typing psr.
Monday, April 2, 2012
Travel Agency , Travel management Project In C++

Hey friends this is a program for travel agency management written in c++ ,, If you are looking for this kind of code surely it will help you. hope you will enjoy it.
download source code:-
| http://www.adrive.com/public/z3mNmC/travel.cpp |
Ardamax Keylogger
Ardamax Keylogger full version with patch:
Ardamax Keylogger is a keystroke recorder that captures user's activity and saves it to an encrypted log file. The log file can be viewed with the powerful Log Viewer. Use this tool to find out what is happening on your computer while you are away, maintain a backup of your typed data automatically or use it to monitor your kids. Also you can use it as a monitoring device for detecting unauthorised access. Logs can be automatically sent to your e-mail address, access to the keylogger is password protected. Besides, Ardamax Keylogger logs information about the Internet addresses the user has visited.
This invisible spy application is designed for 2000, XP, 2003, Vista and Windows 7.
Keylogger Features:
- Email log delivery - keylogger can send you recorded logs through e-mail delivery at set times - perfect for remote monitoring!
- FTP delivery - Ardamax Keylogger can upload recorded logs through FTP delivery.
- Network delivery - sends recorded logs through via LAN.
- Clipboard logging - capture all text copied to the Windows Clipboard.
- Invisible mode makes it absolutely invisible to anyone. Ardamax Keylogger is not visible in the task bar, system tray, Windows 2000/XP/2003/Vista/Windows 7 Task Manager, process viewers (Process Explorer, WinTasks etc.), Start Menu and Windows Startup list.
- Visual surveillance - periodically makes screenshots and stores the compressed images to log.
- Chat monitoring - Ardamax Keylogger is designed to record and monitor both sides of a conversation in following chats:
- AIM
- Windows Live Messenger 2011
- ICQ 7
- Skype 4
- Yahoo Messenger 10
- Google Talk
- Miranda
- QiP 2010
- Security - allows you to protect program settings, Hidden Mode and Log file.
- Application monitoring - keylogger will record the application that was in use that received the keystroke!
- Time/Date tracking - it allows you to pinpoint the exact time a window received a keystroke!
- Powerful Log Viewer - you can view and save the log as a HTML page or plain text with keylogger Log Viewer.
- Small size – Ardamax Keylogger is several times smaller than other programs with the same features. It has no additional modules and libraries, so its size is smaller and the performance is higher.
- Ardamax Keylogger fully supports Unicode characters which makes it possible to record keystrokes that include characters from Japanese, Chinese, Arabic and many other character sets.
- It records every keystroke. Captures passwords and all other invisible text.
Other Features:
- Windows 2000/2003/XP/Vista/Windows 7 support
- Monitors multi-user machines
- Automatic startup
- Friendly interface
- Easy to install
Download Link:-
Wednesday, March 28, 2012
Play music in c
Hey friends it's very interesting to play some music in c language as all we know we can produce sound in c programs like "beep" but if we can sequencing these beep in some order we can make really good sound.
Hope u will enjoy this one ......
code is here ..
//////////////////music////////////////////////
#include<stdio.h>
#include<conio.h>
#include<dos.h>
void main()
{
clrscr();
float maz[10]={130,146.83,164.81,174.61,196,220,246.94};
int n,i;
for(i=0;i<10;i++)
{
sound(maz[i] * 4);
delay(100);
}
nosound();
}
Tuesday, March 20, 2012
Data structure interview questions
This is specially for you all my friend.
Some of the best aptitude question on data-structure hope you will enjoy this E-book .
And please if you are going to download this book please recommend this page on Google by pressing
g+1 button it's a request to all of you my friends...
download:-
http://www.mediafire.com/download.php?53827v6hntvc4ji
Thursday, March 15, 2012
Theory of computation ebook
In
theoretical computer science, the theory of computation is the branch that
deals with whether and how efficiently problems can be solved on a model of
computation, using analgorithm. The field is divided into three major branches:
automata theory, computability theory and computational complexity theory.
In order to
perform a rigorous study of computation, computer scientists work with a
mathematical abstraction of computers called a model of computation. There are
several models in use, but the most commonly examined is the Turing machine.
Computer scientists study the Turing machine because it is simple to formulate,
can be analyzed and used to prove results, and because it represents what many
consider the most powerful possible "reasonable" model of
computation. It might seem that the potentially infinite memory capacity is an
unrealizable attribute, but any decidable problem solved by a Turing machine
will always require only a finite amount of memory. So in principle, any
problem that can be solved (decided) by a Turing machine can be solved by a
computer that has a bounded amount of memory.
for solving all these problem related to toc
this is a book for all of you....
this is a book for all of you....
Introduction to the Theory of Computation by Michael Sipser.
Sunday, March 4, 2012
IDM 6.09 final with patch
Internet Download Manager (IDM) is a tool to increase download speeds by up to 5 times, resume and schedule downloads. Comprehensive error recovery and resume capability will restart broken or interrupted downloads due to lost connections, network problems, computer shutdowns, or unexpected power outages. Simple graphic user interface makes IDM user friendly and easy to use.Internet Download Manager has a smart download logic accelerator that features intelligent dynamic file segmentation and safe multipart downloading technology to accelerate your downloads. Unlike other download managers and accelerators Internet Download Manager segments downloaded files dynamically during download process and reuses available connections without additional connect and login stages to achieve best acceleration performance.
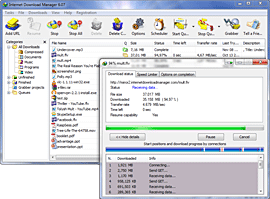 Internet Download Manager supports proxy servers, ftp and http protocols, firewalls, redirects, cookies, authorization, MP3 audio and MPEG video content processing. IDM integrates seamlessly into Microsoft Internet Explorer, Netscape, MSN Explorer, AOL, Opera, Mozilla, Mozilla Firefox, Mozilla Firebird, Avant Browser, MyIE2, and all other popular browsers to automatically handle your downloads. You can also drag and drop files, or use Internet Download Manager from command line. Internet Download Manager can dial your modem at the set time, download the files you want, then hang up or even shut down your computer when it's done.
Internet Download Manager supports proxy servers, ftp and http protocols, firewalls, redirects, cookies, authorization, MP3 audio and MPEG video content processing. IDM integrates seamlessly into Microsoft Internet Explorer, Netscape, MSN Explorer, AOL, Opera, Mozilla, Mozilla Firefox, Mozilla Firebird, Avant Browser, MyIE2, and all other popular browsers to automatically handle your downloads. You can also drag and drop files, or use Internet Download Manager from command line. Internet Download Manager can dial your modem at the set time, download the files you want, then hang up or even shut down your computer when it's done.
Subscribe to:
Comments (Atom)